The blog post of today is a bit different than usual, as you can read the full post on the Panda Security blog. Read it here: Yet another ransomware variant
In this post I'm simply adding some additional information and repeating the most important points.
So, there's yet another ransomware variant on the loose. You may call this one Chuingam (chewing gum?) ransomware or Xwin ransomware - pointing to respectively the file with this string 'Chuingam' dropped, or in the latter case the folder on C:\ it creates. Or just another (skiddie) Generic Ransomware.
In the blog post above, I discuss the methodology to encrypt files it uses and how it creates your own personal key, as well as the ransom message and how to recover files (if you're lucky & fast enough).
pgp.exe (PGP) is used to generate the public RSA key. Since pgp.exe requires the RAR password, this is temporarily stored in the file "filepas.tmp" - which is overwritten and deleted, so no chance to recover this file.
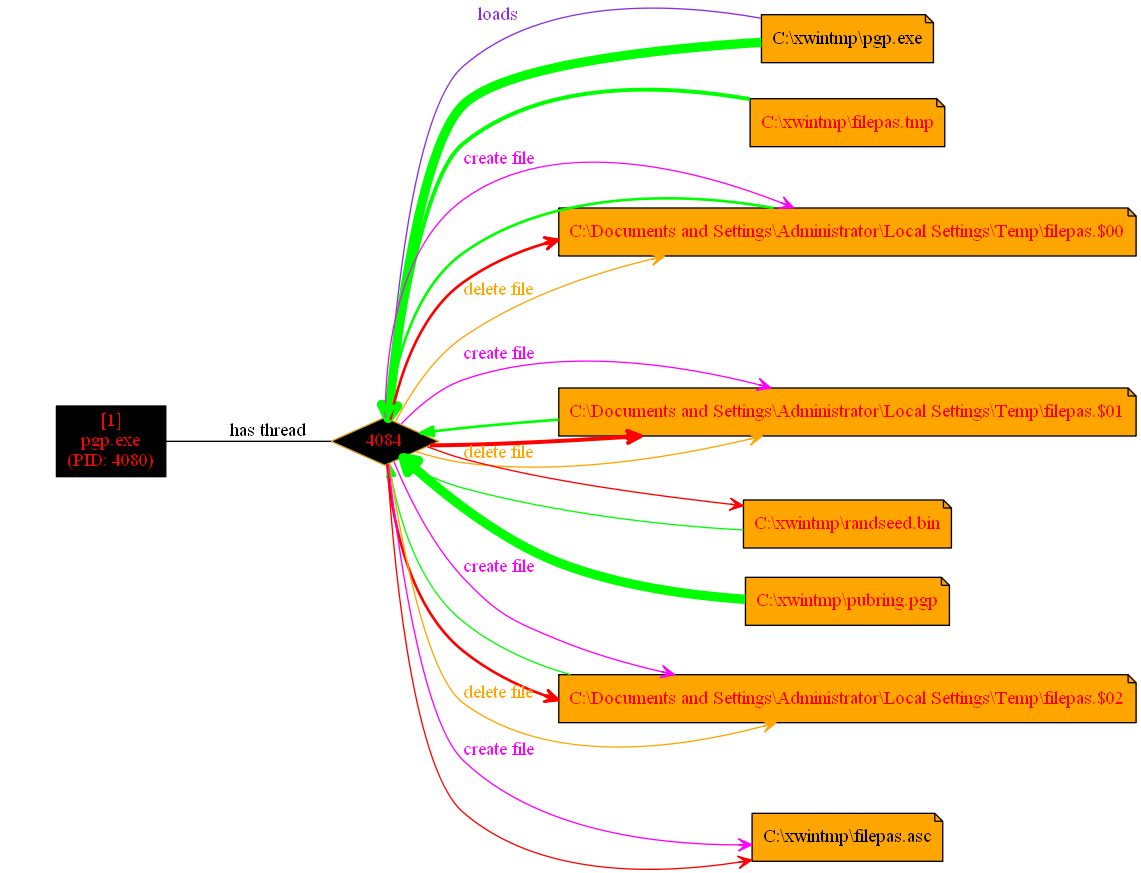 |
| process flow graph of pgp.exe (made using procDOT) |
As a note; it will (try to) encrypt any and all files with the following extensions:
jpg, jpeg, doc, txt, pdf, tif, dbf, eps, psd, cdr, tst, MBD, xml, xls, dwg, mdf, mdb, zip, rar, cdx, docx, wps, rtf, 1CD, 4db, 4dd, adp, ADP, xld, wdb, str, pdm, itdb, pst, ptx, dxg, ppt, pptx
If you've been infected with this ransomware, best thing to do is to either restore from a backup or try to restore previous files (also known as shadow copies).
For additional information in regards to this specific ransomware, refer to:
Yet another ransomware variant
For any further background information on ransomware or further prevention & disinfection advice, I refer to my Q&A on ransomware.
IOCs
Hashes (SHA1)
88039ecb68749ea7d713e4cf9950ffb2947f7683
7e1dd704684f01530307f81bbdc15fe266ffd8db
Domains/IPs
corplawersp.com
5.63.154.90